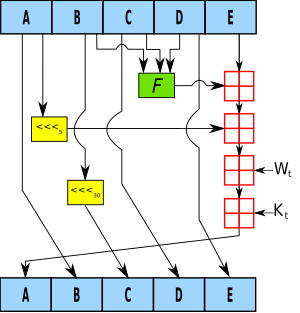
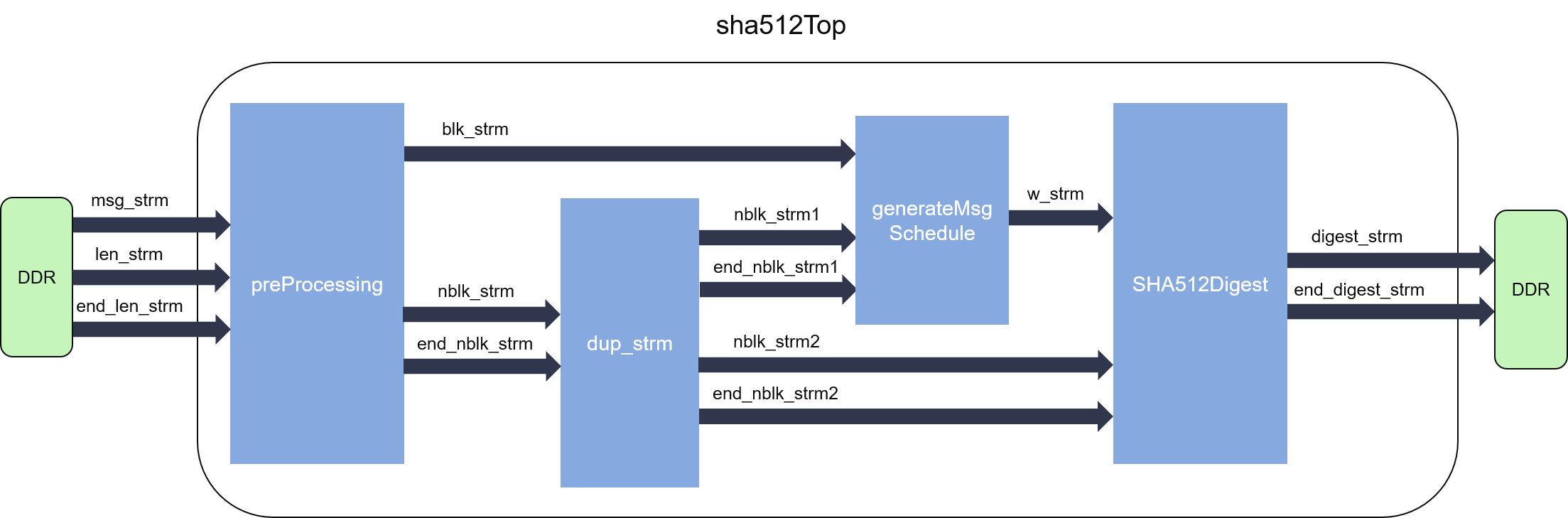
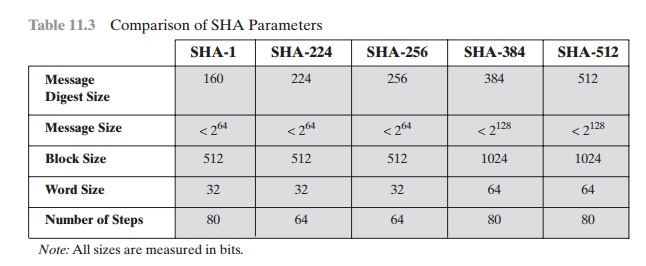
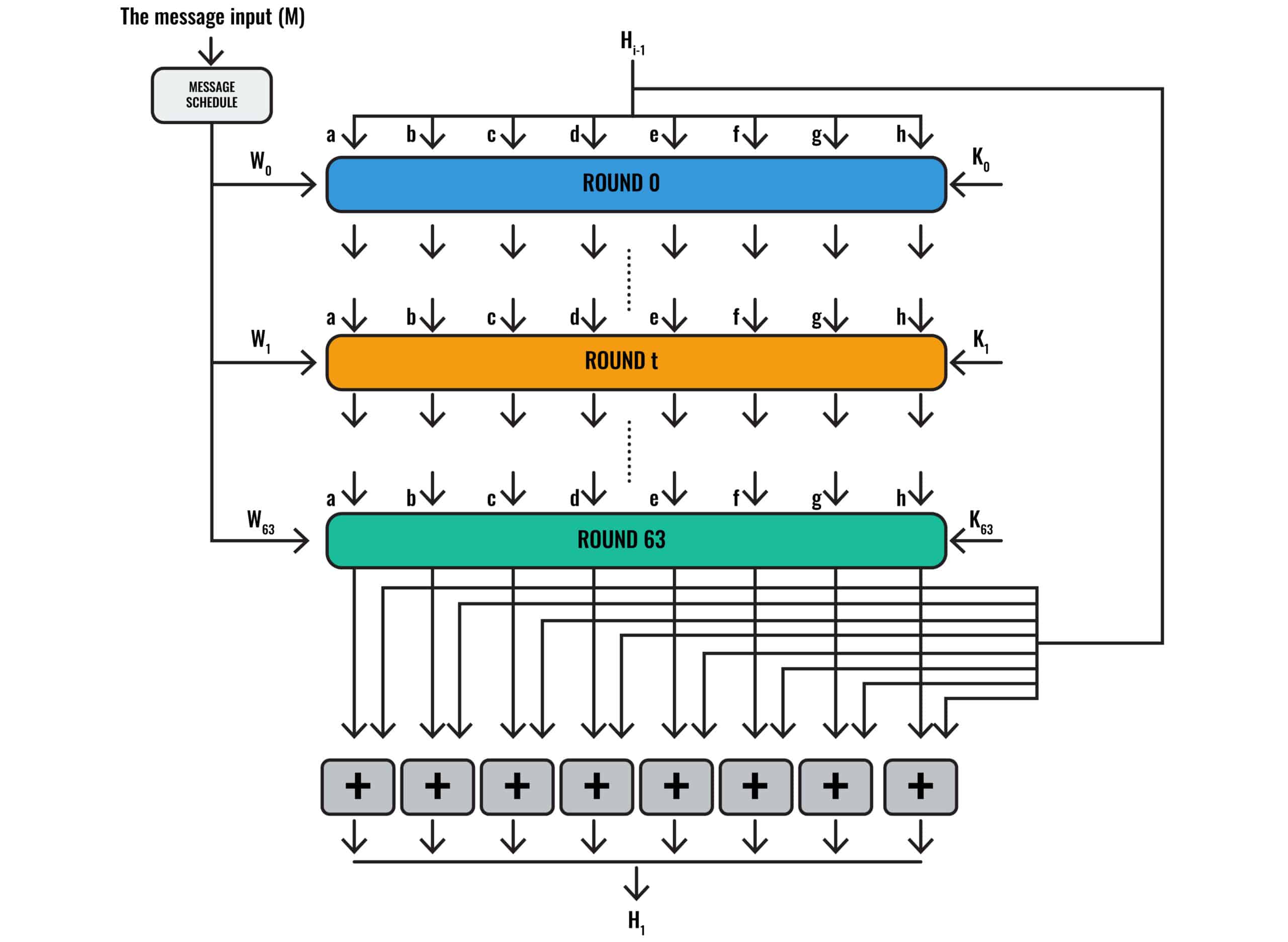
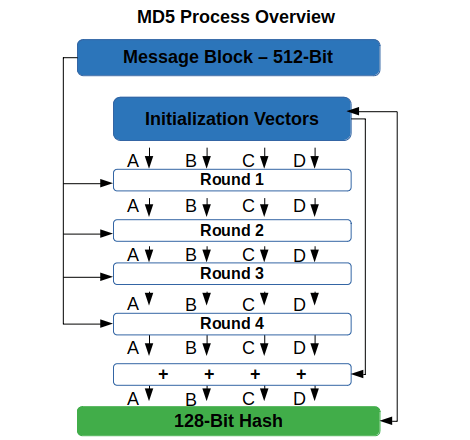
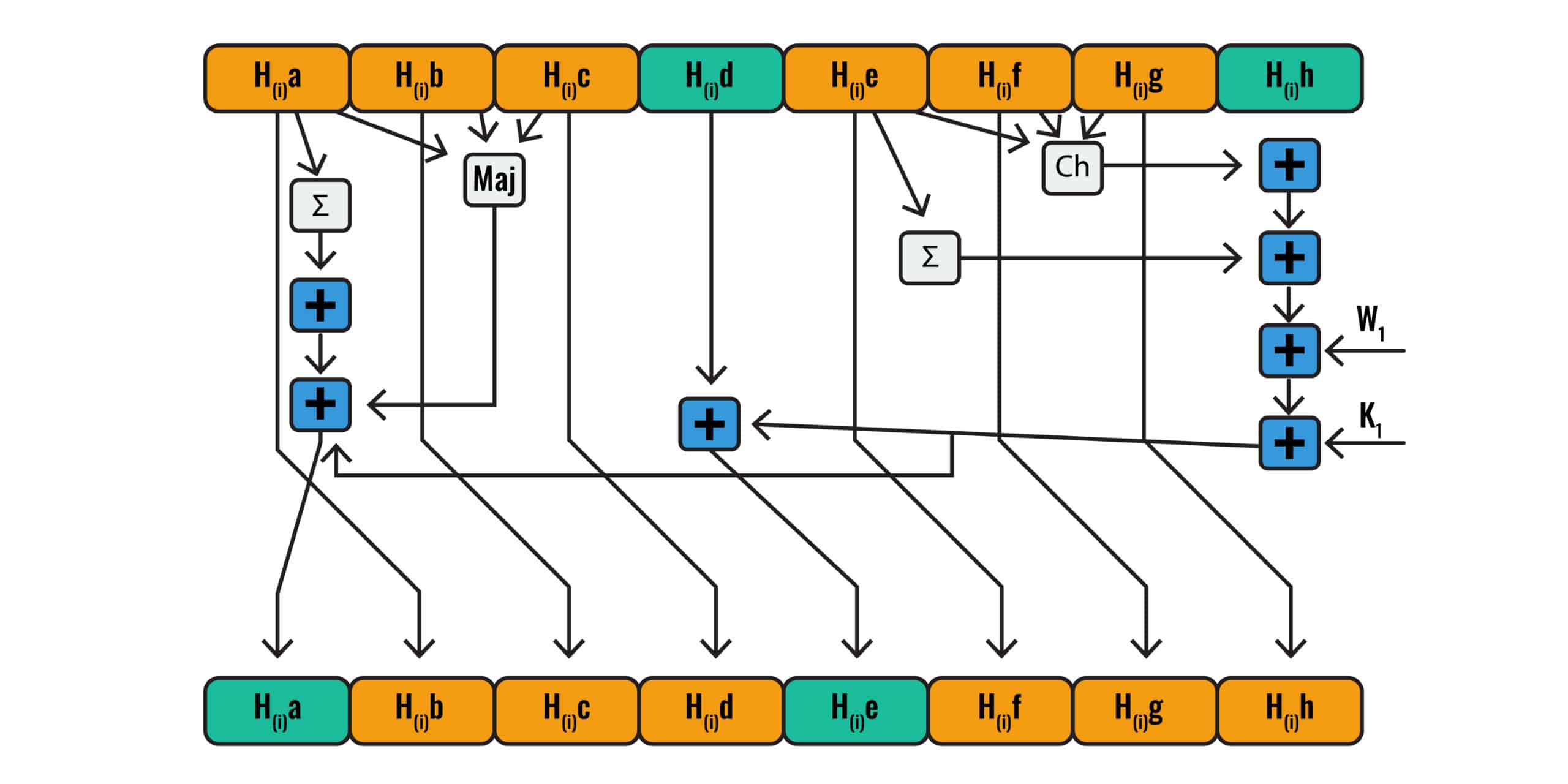
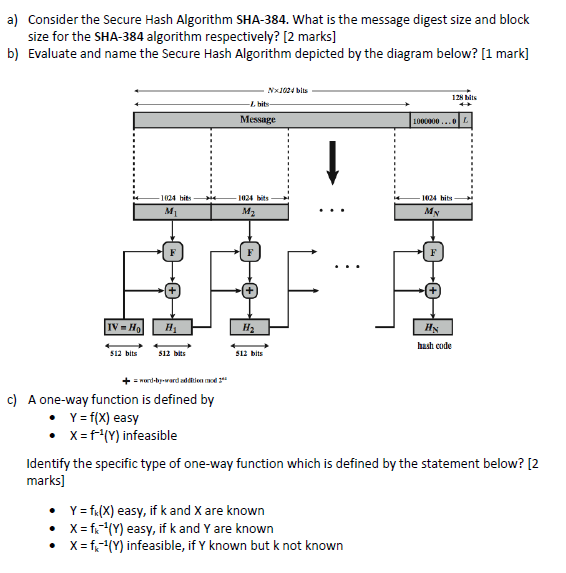
CodeSigningStore on Twitter: "Hash Algorithm Comparison: MD5, SHA-1, SHA-2 & SHA-3 - https://t.co/iaF2MUjuNW The Ultimate Hash Algorithm Comparison: MD5 vs. SHA-1 vs. SHA-2 vs. SHA-3 with their block size, hash digest size,
Analysis of Secure Hash Algorithm (SHA) 512 for Encryption Process on Web Based Application. - Document - Gale Academic OneFile
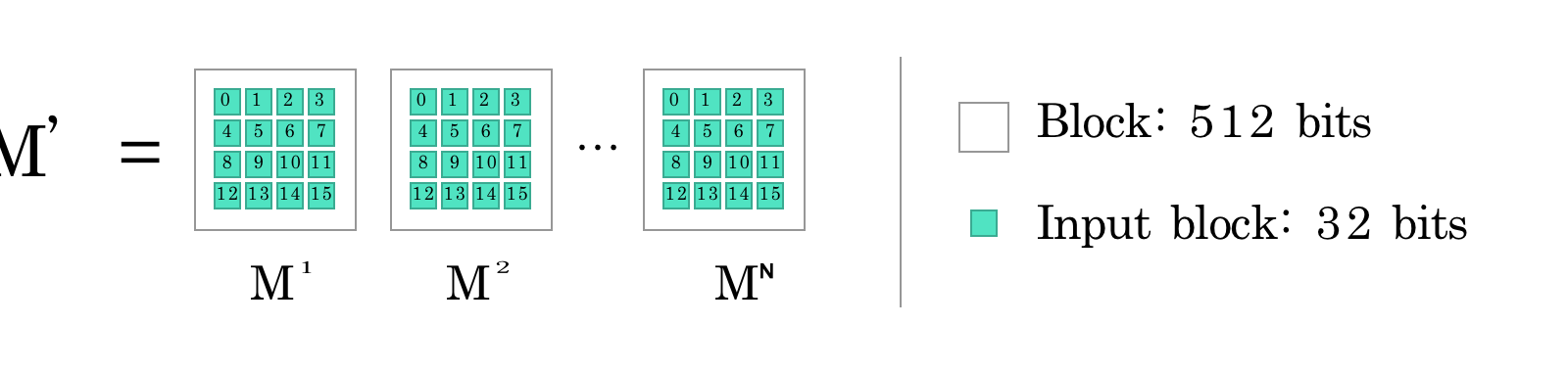
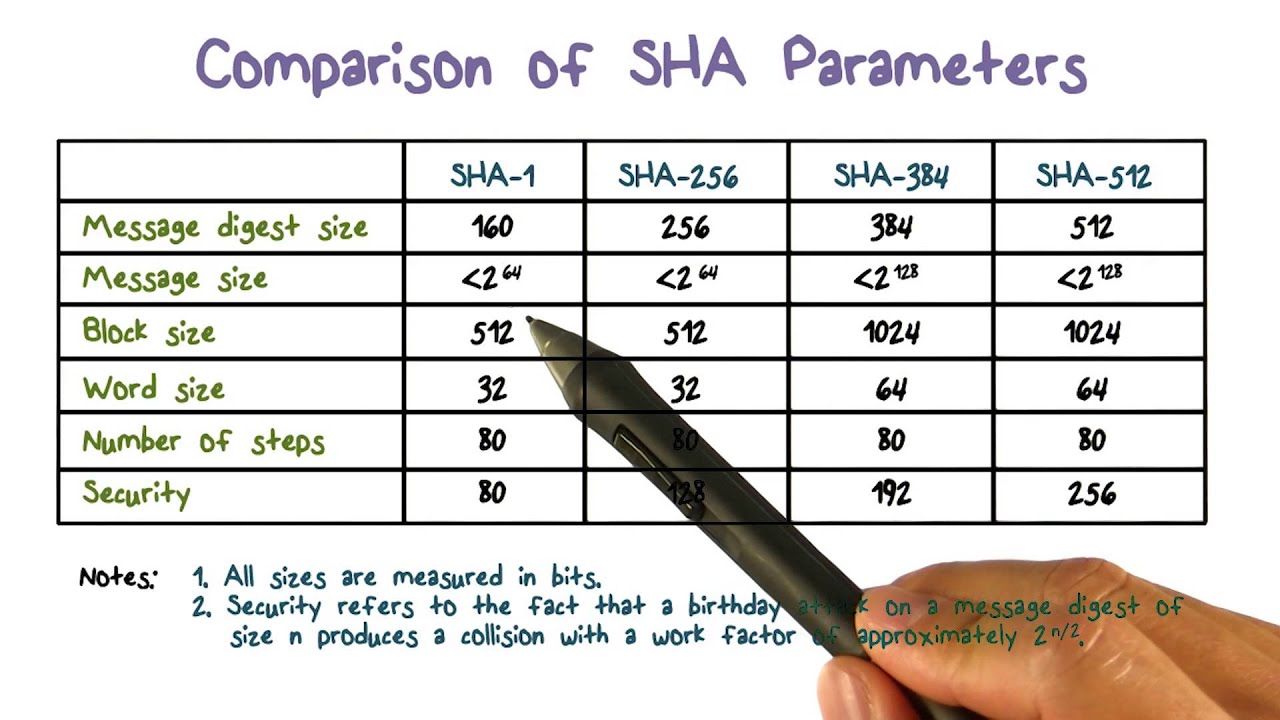
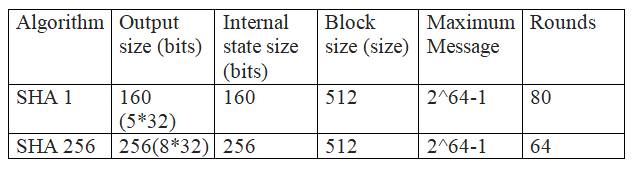



![PDF] Statistical Analysis of the SHA-1 and SHA-2 Hash Functions | Semantic Scholar PDF] Statistical Analysis of the SHA-1 and SHA-2 Hash Functions | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6c2e2ce00039de319b0226a317e75910d6bbb98b/4-Table1-1.png)