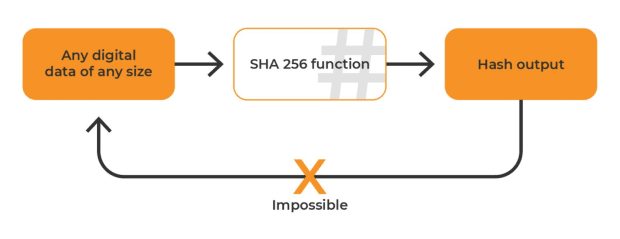
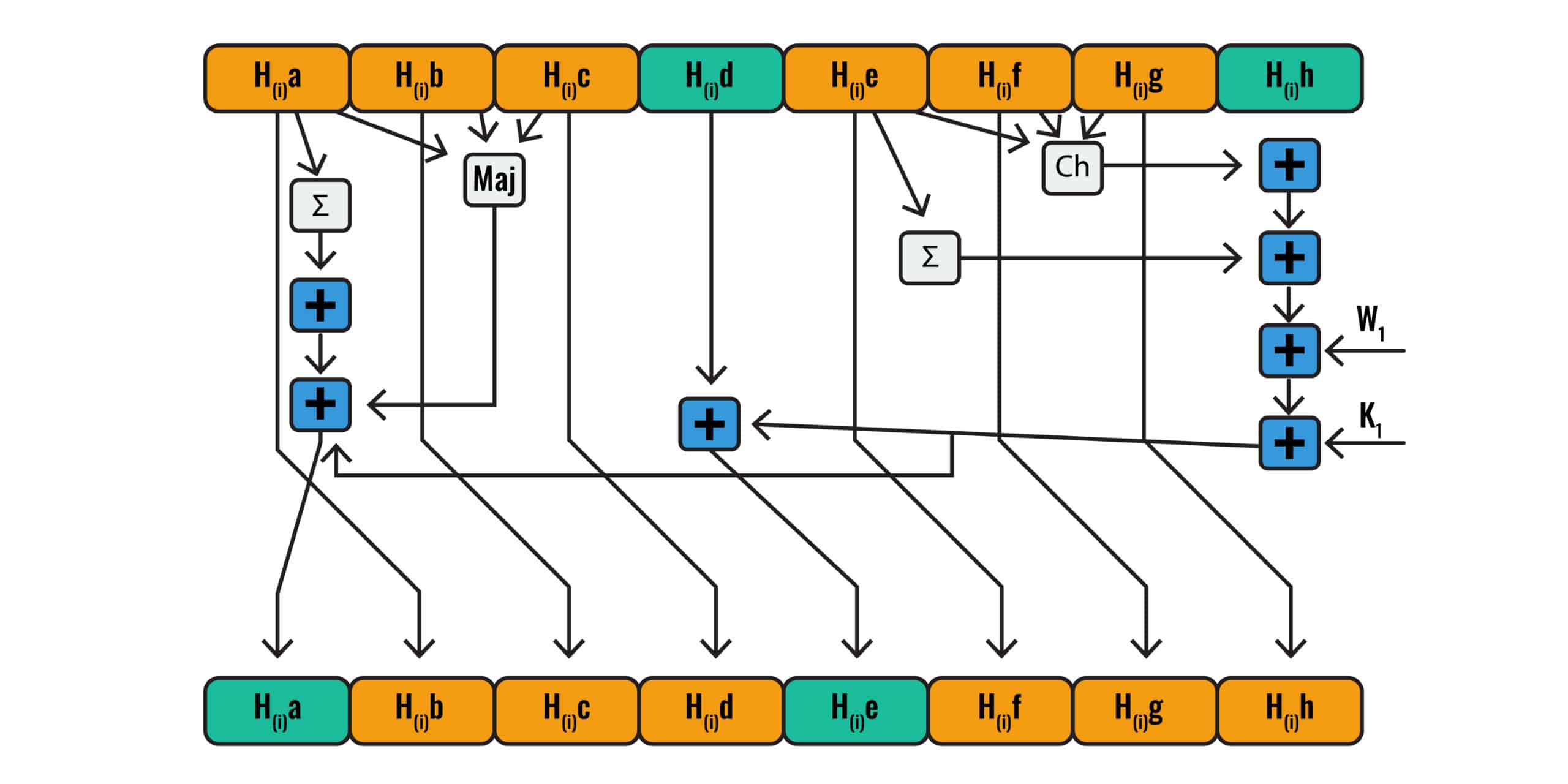
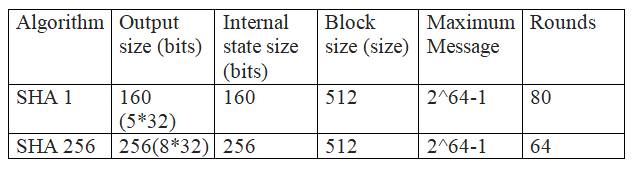
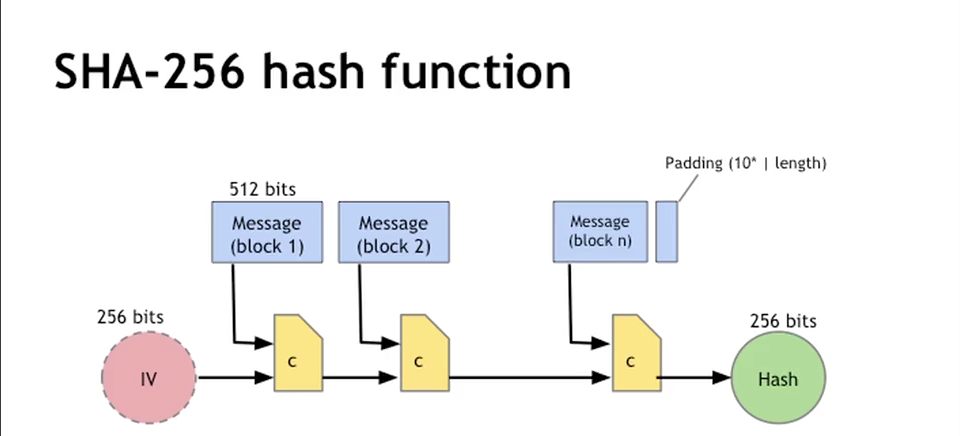
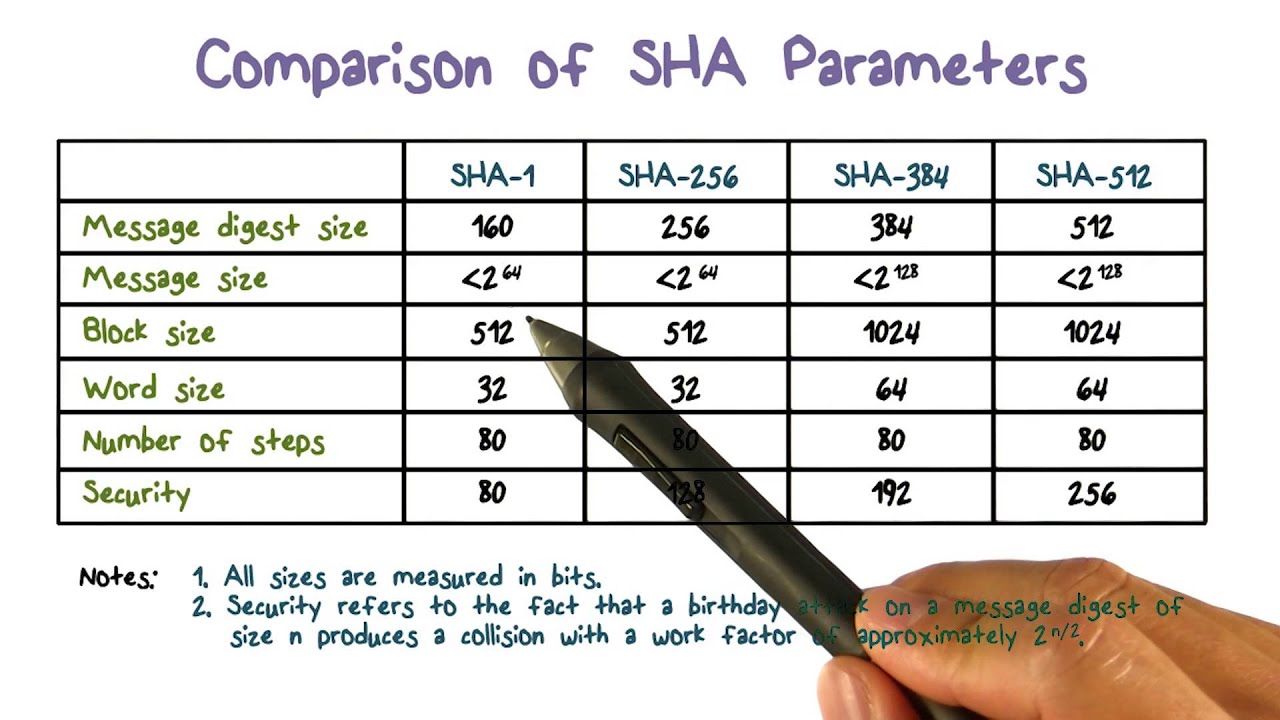
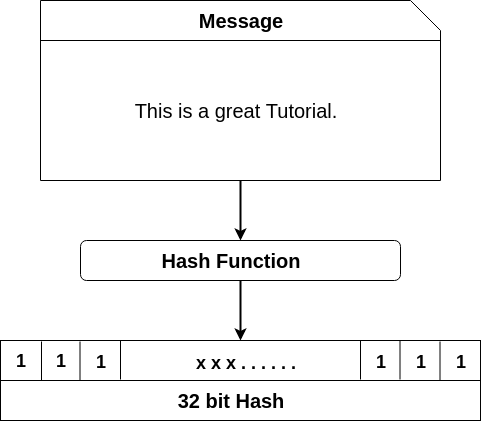
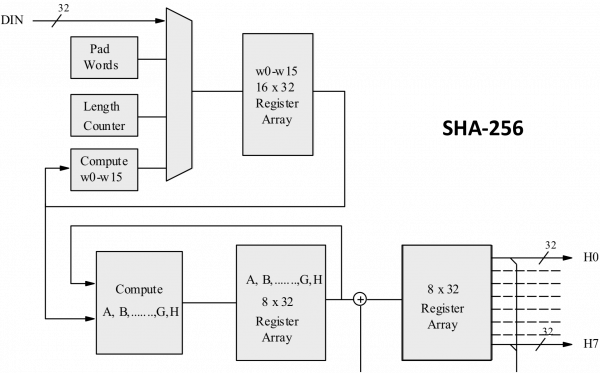
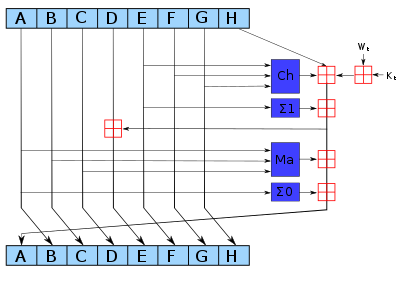
How does the SHA-256 algorithm works? If someone knows how the encryption is done, then how can we say that blockchains are more secured because it is using SHA-256 algorithm for creating
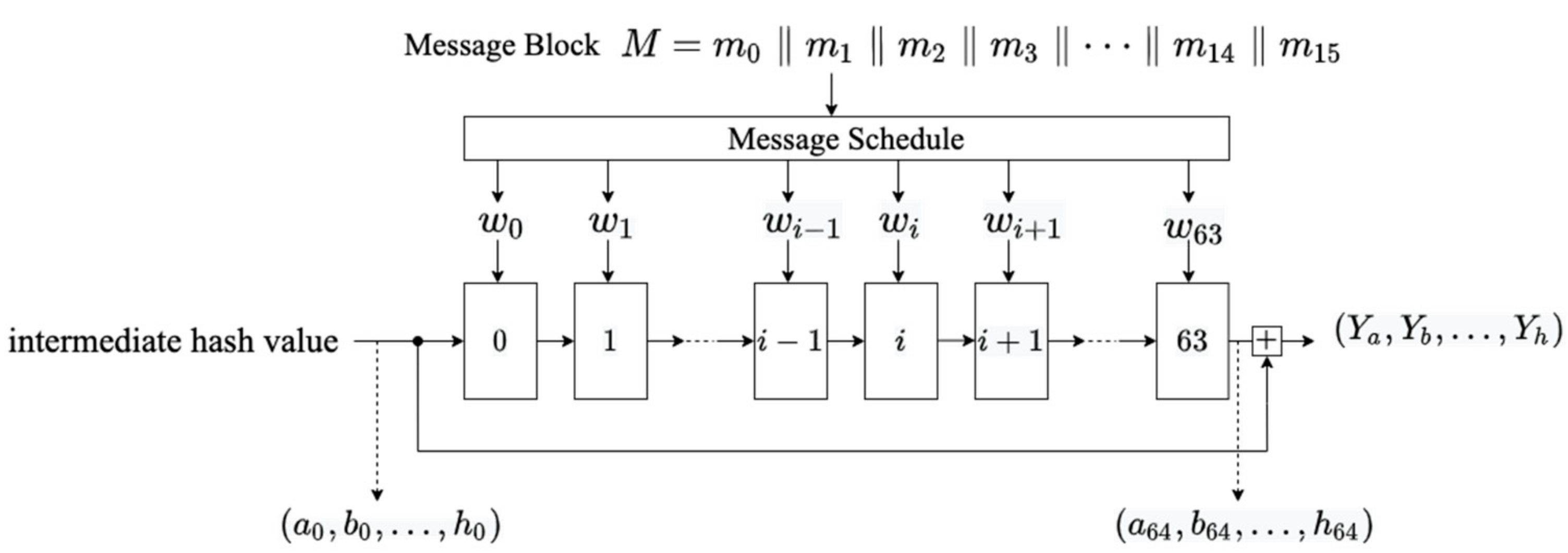
Information | Free Full-Text | Algebraic Fault Analysis of SHA-256 Compression Function and Its Application

Deep dive into SHA-256 (Secure Hash Algorithm 256-bit) | by Radovan Stevanovic | Dec, 2022 | Enlear Academy